While implementing support for RSN Override in WiFi Explorer, we took a closer look at how this mechanism works and why it was introduced. If you’re dealing with interoperability issues in networks that support WPA3 or newer RSN features, RSN Override is something worth understanding.
The Wi-Fi Alliance introduced this mechanism in version 3.4 of the WPA3 Specification to address a growing issue in real-world deployments, where older client devices fail to connect to modern access points because the RSNE and RSNXE have been extended to support newer capabilities. The WPA3 Specification defines the requirements and behaviors for implementing WPA3, the latest generation of Wi-Fi security, including features like SAE for stronger password-based authentication, 192-bit enterprise security, and Enhanced Open for encrypted open networks.
The Problem
Access points advertise their supported security configuration through the RSNE (Robust Security Network Element) and optionally the RSNXE (RSN Extension Element). These include details such as the supported AKM (Authentication and Key Management) suite selectors, pairwise cipher suite selectors, and extended capabilities, such as SAE H2E.
As new features are added to Wi-Fi, these elements become increasingly complex. Some older STAs were not designed to handle multiple AKM selectors or extended RSNXE fields. The result is that they either fail to connect or crash when attempting to parse these elements. Since not all legacy devices can be updated, this creates a deployment challenge for networks that want to adopt WPA3 or more secure configurations without breaking support for existing devices.
The Proposed Solution: RSN Override
RSN Override enables an access point to advertise a simplified RSN configuration for compatibility purposes, while still allowing advanced security features to be enabled for capable devices. It does this by separating the RSN information into multiple elements:
-
RSNE and RSNXE contain only the most basic or widely supported configuration. For example, an access point might advertise only WPA2 with CCMP and a single AKM in these elements. This ensures that older STAs can still parse and connect successfully.
-
RSNE Override provides a more complete set of RSN parameters, including support for WPA3, SAE, or other newer features. STAs that support RSN Override will look for this element and use it instead of relying solely on the RSNE.
-
RSNE Override 2 is used when the administrator wants to further reduce the number of AKM and cipher suite selectors in each element or when managing multi-link devices. This element allows even more precise control over what is advertised, especially in the context of Wi-Fi 7 Multi-Link Devices (MLDs), which can use RSNE Override 2 to advertise common security parameters across all links.
-
RSNXE Override elements extend this concept to the RSNXE, allowing the access point to advertise extended capabilities separately. However, this element must not be used unless RSNE Override is already present.
These override elements are not standard RSNE or RSNXE fields. Instead, they are encoded inside Wi-Fi Alliance vendor-specific elements using predefined OUI types and payload formats. Each element contains a payload with the same structure as the corresponding RSNE or RSNXE, allowing newer clients to parse them using existing logic.
Legacy STAs, which are unaware of the override mechanism, ignore these vendor-specific elements and connect using the simplified RSNE or RSNXE. Modern STAs that support RSN Override read the override elements and select the appropriate configuration, including the strongest mutually supported security options.
How It Works in Practice
This mechanism reduces the risk of interoperability failures while preserving support for stronger authentication and encryption methods. For example:
-
A legacy device connects using WPA2-PSK, as advertised in the RSNE.
-
A modern device connects using WPA3-SAE, based on the parameters in the RSNE Override element.
This approach enables the AP to advertise a conservative RSNE for maximum compatibility while using override elements to provide enhanced options to clients that support them. It gives administrators a way to balance compatibility and security across mixed-device environments.
However, the RSN overriding mechanism depends on client support. If a modern STA does not implement RSN Override, it will ignore the vendor-specific override elements and rely only on the standard RSNE and RSNXE. For example, if the RSNE advertises only WPA2-level security such as PSK with CCMP to maintain compatibility with legacy devices, and the WPA3 or SAE options are included only in the override elements, then a STA that does not support RSN overriding will still connect using WPA2, even if both the access point and the STA are capable of WPA3.
This is a tradeoff: RSN Override allows networks to stay compatible with older clients, but newer clients must be override-aware to benefit from the enhanced security options.
That is why the specification recommends using RSN Override only when necessary, typically in environments where legacy STAs are known or expected to have issues with newer RSN capabilities, and where the organization has control over newer devices and can confirm that they support RSN overriding. In these cases, it becomes safe to advertise only a basic configuration in the RSNE for compatibility and place the full set of security options in the override elements. This allows modern devices to use WPA3 without falling back to WPA2, while avoiding connection failures on older clients that cannot handle extended RSNE fields.
What We’re Doing in WiFi Explorer
With support for RSN Override, WiFi Explorer can now detect and decode:
-
When an access point is using RSN Override
-
The contents of the RSNE Override and RSNE Override 2 elements
-
The complete set of AKM and cipher suites being offered across all elements
-
RSNXE and RSNXE Override fields when present
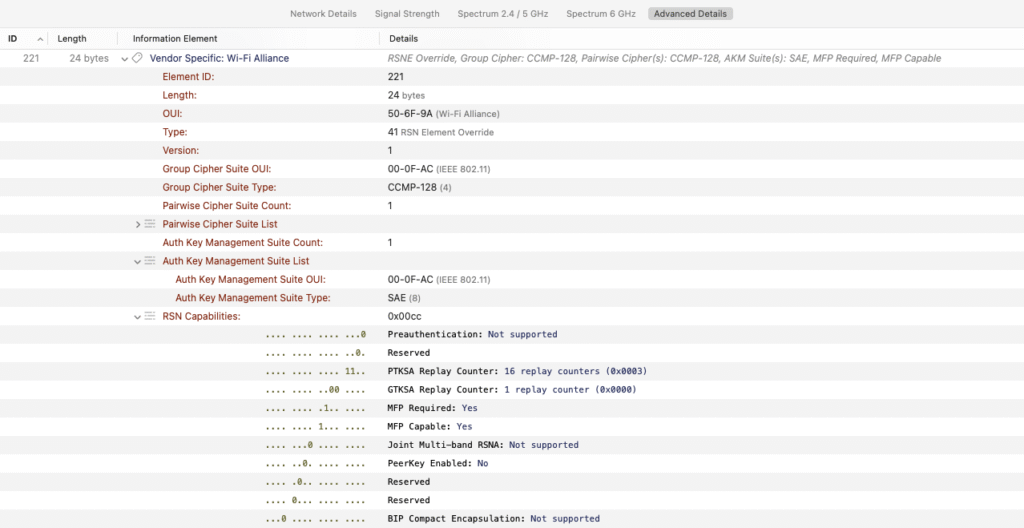
RSNE Override Element
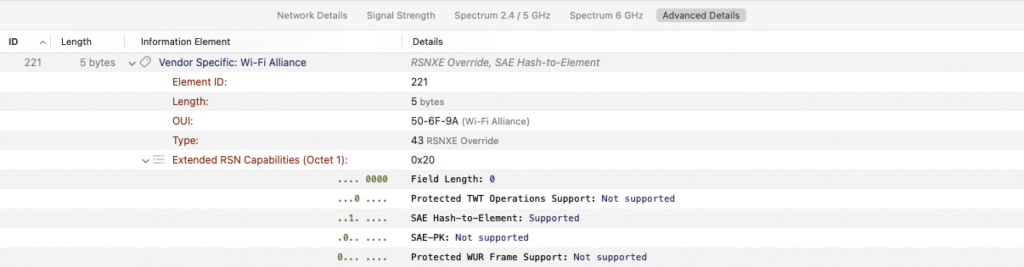
RSNXE Override Element
This helps clarify why some devices may connect using different security configurations, even on the same network. It also provides visibility into what the access point is offering beyond the limited RSNE.
RSN Override provides a practical solution to the challenges of evolving Wi-Fi security in environments that feature a mix of legacy and modern devices. As more networks adopt WPA3 and Wi-Fi 7 features, supporting this mechanism could become essential for maintaining compatibility while still enabling stronger security for capable devices.
Thank for this blog. Have to reread the Specs. I assume that this applies both for PSK and Enterprise nets.
Very well explained Adrian ! Thanks for the clarification.
Clearly explained ! Thanks
Could you please some of the modern clients that can successfully parse these new RSN override /RSN override 2 IEs
Very well explained